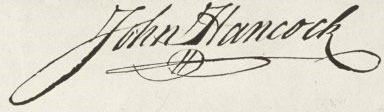Biometric Technologies
Biometrics
Click thumbnail to view full-size




What are Biometrics?
The word itself, Biometrics, is derived from two Greek words.
Bios = life and Metron = measure. So biometrics, as a direct translation, means "measure of life."
In the past "biometrics" meant measuring and logging information on living things. As such it was used as a tool of statistical analysis of life-forms. In forestry, fish population studies, and human population studies. Biometrics originally meant tracking large numbers of similar lifeforms.
Today the word has a slightly different meaning. It is a term used to imply a means of identifying individual humans.
After the multiple terror attacks at the beginning of this new century biometrics took on a new urgency. In fact the science, though still in it's infancy, has already found its place in personal computers as fingerprint scanners; a means of locking and unlocking personal computers by means of a finger scan.
Biometrics
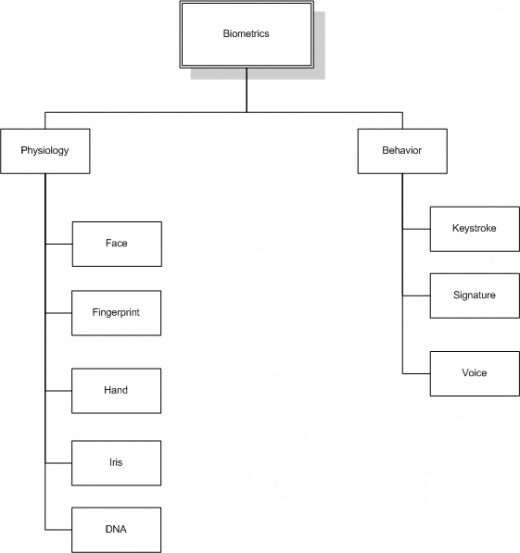
Interests and Concerns
Areas of interest in biometrics fall into two categories; physiological and behavioral. Of course physiological biometrics measure empirical characteristics that are known to be unique from person to person. For example the iris of the eye, fingerprints, facial structure, the hand, and even DNA are known to be unique from person to person.
Behavioral metrics include keystroke patterns on computer keyboards, the signature, and voice analysis.
Both categories have their own advantages and disadvantages. The first and likely most important concern is accuracy. Biometrics must be accurate enough to insure that each subject is positively identified. But truly robust biometric systems can suffer from processing delays.
In other words if a system is fast it may be inaccurate; if accurate processing for that level of accuracy may take entirely too long to be useful.
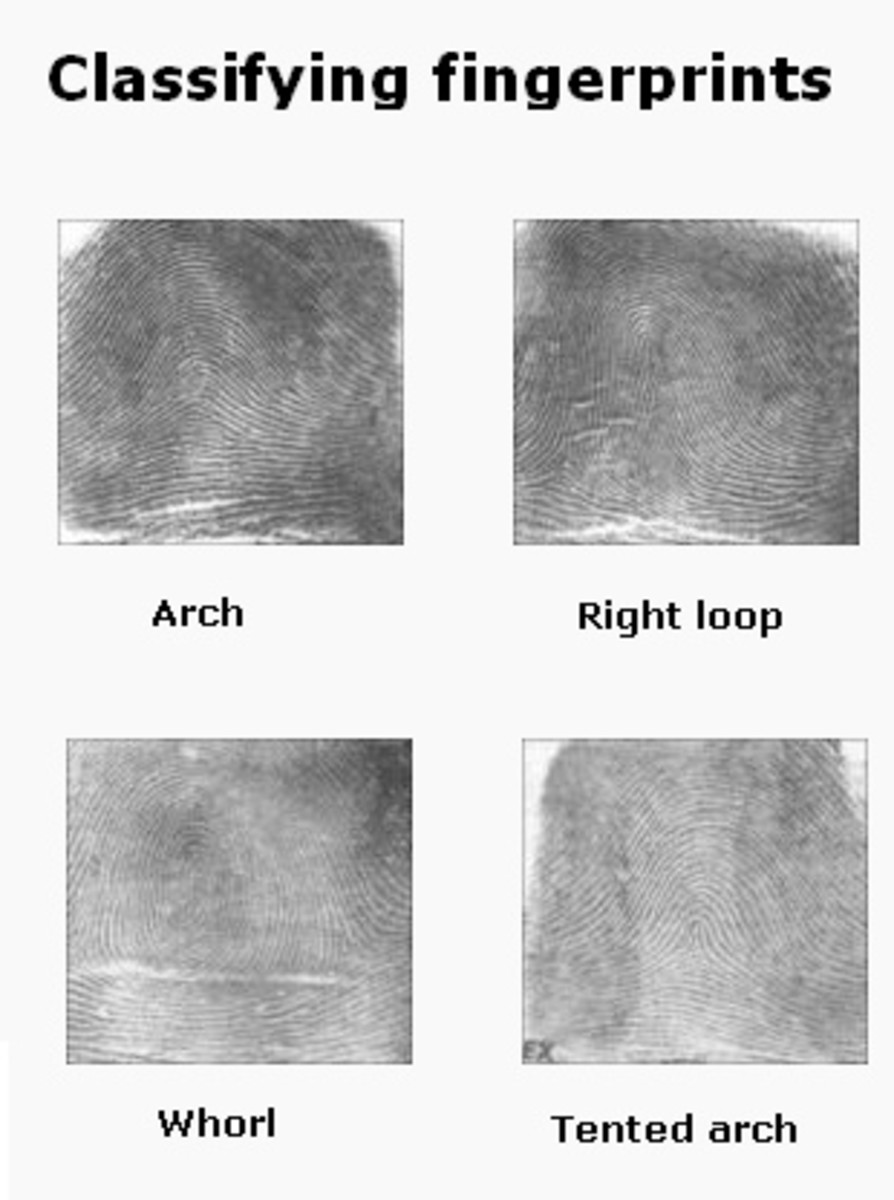
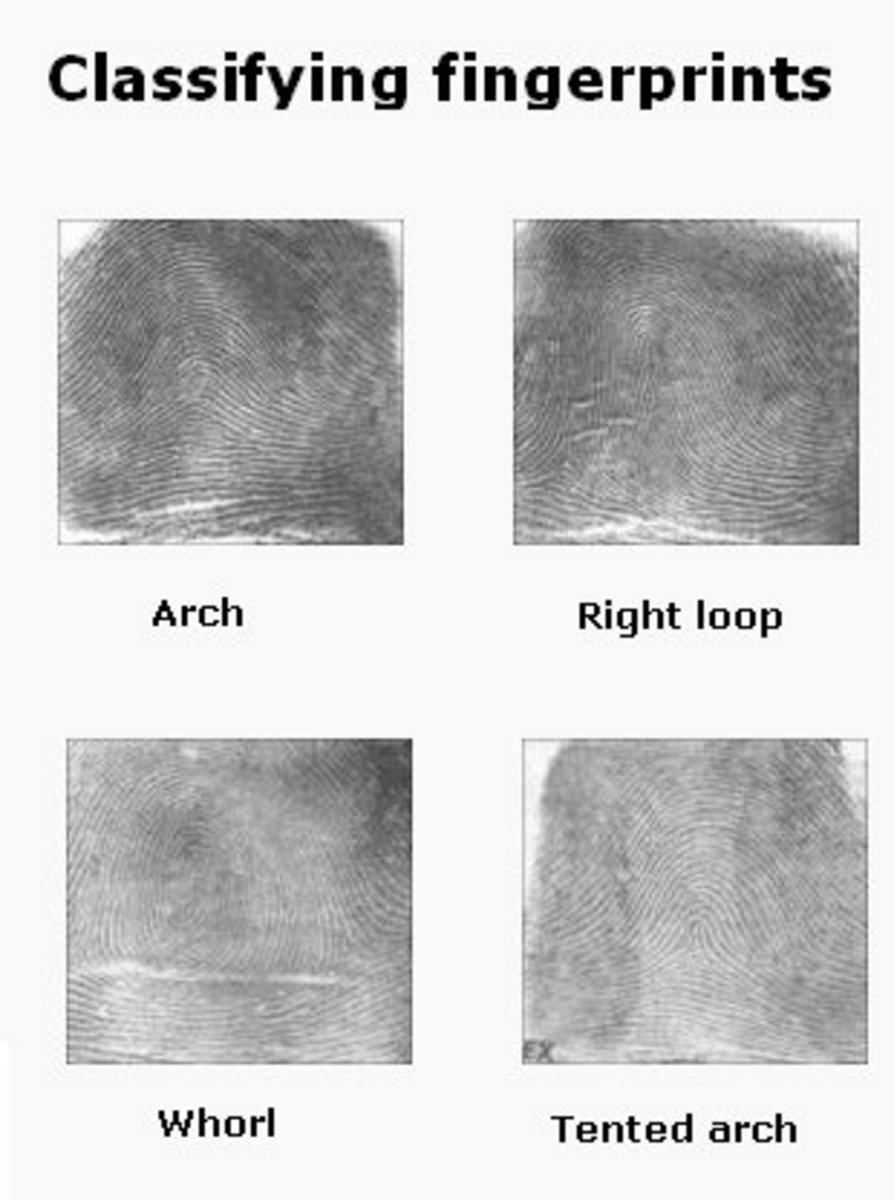
Fingerprint
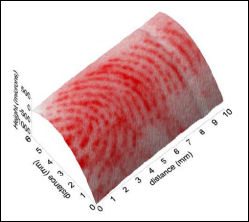
Fingerprint Identification
Fingerprints were first used as identification in 14th Century Persia. it was common practice to place a fingerprint on official documents. A Persian doctor noticed that of all the fingerprints he'd seen no two from different persons were alike. This difference was later noticed by Dr. Henry Faulds in 1880 in the magazine Nature. Dr. Faulds offered his information to the London Metropolitan police, but was dismissed.
Fingerprint analysis is the study of the ridges and valleys left by "friction ridges" on the fingertips. These ridges can also be found on the palm of the hand, the toes, and the feet. Fingerprints are formed during fetal development and do not change (barring scaring or injury) throughout life. In fact fingerprints stay the same even in new layers of skin.
With the advent of computing and scanning technology it is much easier to scan and store fingerprint information and assign that information to persons via name, age, and other biometric data. Databases of this information are kept at various police departments and the Federal Bureau of Investigation.
The FBI currently has a database of over fifty one million fingerprints.
Interestingly there is only one non-primate animal who has similar fingerprints to humans; the koala. In fact, koala fingerprints are so similar to human prints that even scanning electron micrographs can be hard to tell apart.
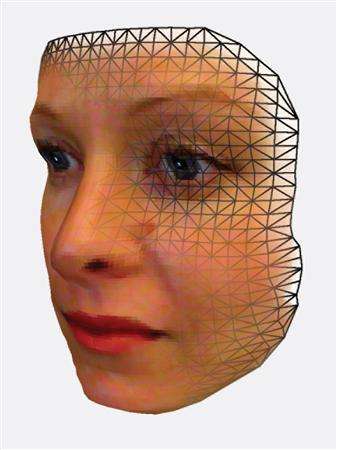
Iris and Face Metrics
Click thumbnail to view full-size

Iris and Facial Identification
The Iris
More recently iris patterns have been used for identification purposes.The iris is thought to be the ideal part of the human body for biometric identification:
- It is well protected from damage and wear unlike fingerprints which can be altered over time
- The iris is flat, compared to the eyeball, and it's diameter is consistent from eye to eye. This makes measuring the patterns of the iris easier since the size itself falls within acceptable limits
- The iris has a very fine texture which is randomly created during embryonic development. As with fingerprints even twins have different iris patterns
- An iris scan is easy to accomplish as well established photographic techniques are all that is required. This also eliminates any direct physical contact between the person being scanned and the scanning equipment
- Algorithms already exist that virtually guarantee a zero percent false identification rate. This system is John Daugman's IrisCode
- Though changes in iris color can occur the patterns themselves are quite stable over many decades
The Face
As with the iris, the advantage with facial recognition is that standard photographic techniques can be used to record the human face. With the photograph an operator can extract the coordinates of facial features such as the distance between the center of pupils, the inside metric from the corners of eyes, the outside corner of eyes, the patern of the hairline and the like.
From these measurements a list of twenty distances are calculated and placed into a set of formulas.
There are inherent problems with this though in that it is unlikely that any two pictures would be the same. Head rotation, tilt, lean, and scale all play a part. To counter these problems each set of distances is standardized to represent the face in a full frontal orientation. To get to this point of standardization computer programs first try to determine tilt, lean, and rotation and then, using angular calculations, determine the coordinates of the twenty points described above.
The advantages are;
- The subject is much less likely to know that their face is being scanned
- It is non-intrusive to the subject
- Lends itself to public settings such as airports and train stations
- Is much non-intrusive to the public at large
DNA
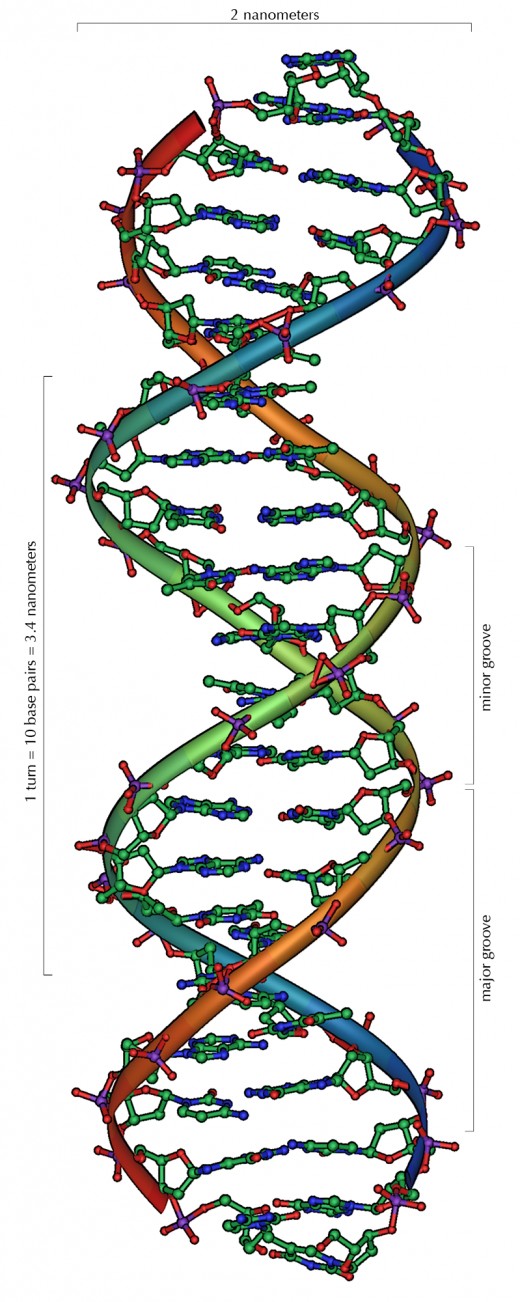
DNA Identification
Though this seems to be the most reliable form of measure time and testing have proven it's not. This technology may well get the innocent out of jail and make cases against the guilty easier to prosecute, but the fact is that about one point five percent of the Earth's population are monozygotic twins.
This may seem odd since the very same monozygotic (identical) twins will have different finger and iris prints.
There is also a time factor. DNA analysis still takes days if not weeks to accurately perform.
Behavioral Biometrics
Click thumbnail to view full-size
Behavioral Biometrics
Keystroke
Also called "typing dynamics" measure the amount of time between keystrokes as well as the timing of a key being pressed and released.
This biometric uses the rhythm which an individual uses as s/he types characters on a keyboard or keypad. These rhythms are measured to develop a unique biometric signature the persons typing pattern for future reference.
Raw data can be recorded to determine Dwell time (the amount of time taken to press a key) and Flight time (the time between each key-press). The recorded keystroke timing data can then be processed through an algorithm, to determine the a primary typing pattern for future comparison.
Signature
Though in the past this has been a good measure of a person's identity advances in scanning technologies has made this particular means of identification unreliable.
For example member of congress can now have their signatures stored as "true type" fonts. This allows Congress-persons to "sign" documents quickly and electronically.
Voice
Also known as speaker recognition this means of identification is forty years old.
Speaker recognition uses the acoustic features of speech that have been found to differ between individuals. These acoustic differences are caused by both anatomy and upbringing. For example the size and shape of the throat and mouth can affect the acoustic characteristics of the speaker. Voice pitch and speaking style (learned behaviors) can also be measured.
The advantages to speaker recognition are;
- Is non invasive and the speaker can be unaware that identification it taking place
- Non intrusive. No physical contact with the detection equipment is required
Disadvantages include;
- Multiple simultaneous speakers can muddle the identification
- A previous recording must be available for comparison
- Ambient noise can muddle or even obliterate the voice
- Voice changes can occur due to aging or injury